In this blog, I will teach you how to perform SQL injection in Ethical Hacking using a real-world example. You will be able to determine whether a website is vulnerable to SQL injection, obtain data from the web apps database, and compromise a database.
Ethical hackers, like other computer and network security roles, are in high demand, and this demand is only increasing as the severity and cost of cyber-attacks rise.
So join the Ethical Hacking Course in Kochi to enhance your skills and knowledge.
What is SQL injection?
SQL injection is a type of attack in which the attacker sends a specially crafted SQL query (statement) to a database server and modifies the database. When user input is not properly sanitized before being used in a SQL query, a SQL injection occurs.
The vulnerability can be exploited by providing input through the user interface or hidden fields; however, if user input is used for parameters such as a name or an id, those parameters should also be validated to ensure that no invalid input is used.
Ethical Hacking Course in Ahmedabad at FITA Academy teaches students how to exploit and eliminate vulnerabilities for an enterprise legally.
How Does SQL Injection Work?
In a vulnerable server, an attacker can modify a user-supplied parameter in order to run arbitrary SQL code or commands on the back-end database. This type of attack can be carried out in a variety of ways.
For example, in the user login screen, the dynamic fields where users enter data are username and password. Dynamic queries will be created based on the user’s inputs; the standard query will be used.
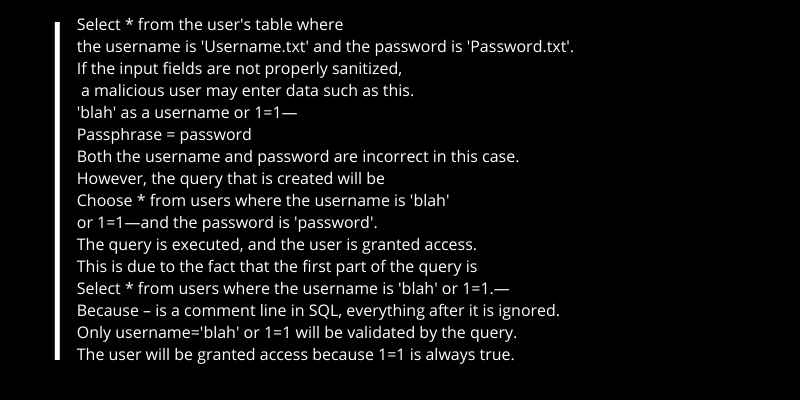
An SQL injection attack can be carried out with the following goals:
- To dump a system’s entire database,
- To change the database content, or
- To run various queries that the application does not permit.
This type of attack occurs when applications fail to properly validate inputs before passing them to a SQL statement. In most cases, injections are placed in address bars, search fields, or data fields.
The simplest way to determine whether a web application is vulnerable to a SQL injection attack is to insert the “‘” character into a string and see if an error occurs.
Conclusion
As we discussed SQL injection in Ethical Hacking its definition with an example, how it works, and its attacks. Ethical hacking is the method of compromising computer systems in order to assess their protection while acting in good faith by informing the vulnerable party. Ethical hacking is a necessary skill for many job roles involving the protection of an organization’s online assets. To gain skills about Ethical hacking enroll in Ethical Hacking Course in Delhi.